OPENVPN多地组网
最近接到一个新需求:因为网络设备不是我们管理,管理方由于安全考虑不允许做VPN组网。在这种情况下如何实现VPN互联,使多个独立网络内网互通。
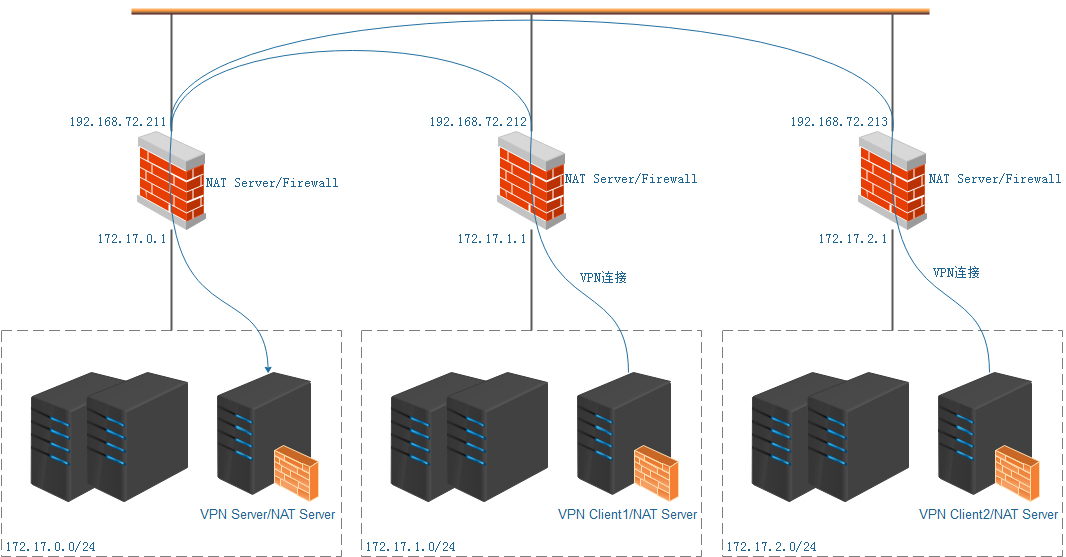
网络结构如下所示:
安装OPENVPN软件:
在VPN Server、VPN Client1、VPN Client2上安装OPENVPN软件包:
yum install epel-release -y
yum install openvpn配置证书:
在VPN Server上安装easy_rsa:
yum install easy-rsa -y配置证书:
mkdir -p /etc/openvpn/easy-rsa
cp -fr /usr/share/easy-rsa/3/* /etc/openvpn/easy-rsa/
cd /etc/openvpn/easy-rsa/
./easyrsa init-pki
./easyrsa build-ca nopass
./easyrsa build-server-full server nopass
./easyrsa build-client-full client1 nopass
./easyrsa build-client-full client2 nopass
./easyrsa gen-dh
openvpn --genkey --secret ta.key创建VPN运行所需目录:
mkdir /var/log/openvpn
chown openvpn:openvpn /var/log/openvpn
mkdir -p /etc/openvpn/ccdVPN Server 配置:
编辑/etc/openvpn/server.conf
# Which local IP address should OpenVPN
# listen on? (optional)
;local a.b.c.d
port 1194
# TCP or UDP server?
;proto tcp
proto udp
;dev tap
dev tun
;dev-node MyTap
ca /etc/openvpn/easy-rsa/pki/ca.crt
cert /etc/openvpn/easy-rsa/pki/issued/server.crt
key /etc/openvpn/easy-rsa/pki/private/server.key # This file should be kept secret
dh /etc/openvpn/easy-rsa/pki/dh.pem
;topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist /etc/openvpn/ipp.txt
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
;server-bridge
push "route 172.17.0.0 255.255.255.0"
client-config-dir /etc/openvpn/ccd
route 172.17.1.0 255.255.255.0
route 172.17.2.0 255.255.255.0
;learn-address ./script
;push "redirect-gateway def1 bypass-dhcp"
;push "dhcp-option DNS 208.67.222.222"
;push "dhcp-option DNS 208.67.220.220"
client-to-client
;duplicate-cn
keepalive 10 120
tls-auth /etc/openvpn/easy-rsa/ta.key 0 # This file is secret
cipher AES-256-CBC
;compress lz4-v2
;push "compress lz4-v2"
comp-lzo
;max-clients 100
user openvpn
group openvpn
persist-key
persist-tun
status /var/log/openvpn/status.log
log /var/log/openvpn/server.log
log-append /var/log/openvpn/server.log
verb 3
;mute 20
explicit-exit-notify 1编辑/etc/openvpn/ccd/client1
ifconfig-push 10.8.0.6 255.255.255.0
iroute 172.17.1.0 255.255.255.0
push "route 172.17.2.0 255.255.255.0"编辑/etc/openvpn/ccd/client2
ifconfig-push 10.8.0.8 255.255.255.0
iroute 172.17.2.0 255.255.255.0
push "route 172.17.1.0 255.255.255.0"VPN Client 配置:
编辑/etc/openvpn/client.conf
client
;dev tap
dev tun
;dev-node MyTap
;proto tcp
proto udp
remote 192.168.72.211 1194
;remote my-server-2 1194
;remote-random
resolv-retry infinite
nobind
user openvpn
group openvpn
persist-key
persist-tun
;http-proxy-retry # retry on connection failures
;http-proxy [proxy server] [proxy port #]
;mute-replay-warnings
ca /etc/openvpn/ca.crt
cert /etc/openvpn/client.crt
key /etc/openvpn/client.key
remote-cert-tls server
tls-auth /etc/openvpn/ta.key 1
cipher AES-256-CBC
comp-lzo
verb 3
;mute 20拷贝证书文件:
在VPN Server上拷贝ca.crt、client1.crt、client1.key、ta.key文件到VPN Client1,并将client1.crt改名client.crt,client1.key改名client.key。
在VPN Server上拷贝ca.crt、client2.crt、client2.key、ta.key文件到VPN Client2,并将client2.crt改名client.crt,client2.key改名client.key。
配置静态路由:
172.17.0.0/24段机器:
编辑/etc/sysconfig/static-routes
any net 172.17.1.0/24 gw 172.17.0.101
any net 172.17.2.0/24 gw 172.17.0.101172.17.1.0/24段机器:
编辑/etc/sysconfig/static-routes
any net 172.17.0.0/24 gw 172.17.1.101
any net 172.17.2.0/24 gw 172.17.1.101172.17.2.0/24段机器:
编辑/etc/sysconfig/static-routes
any net 172.17.0.0/24 gw 172.17.2.101
any net 172.17.1.0/24 gw 172.17.2.101配置完成后需要重启网卡才生效,不方便重启的话使用route add -net 172.17.0.0/24 gw 172.17.2.101命令添加。
配置NAT转发:
在VPN Server、VPN Client1、VPN Client2上配置NAT转发规则
VPN Server:
iptables -t nat -A POSTROUTING -s 172.17.0.0/24 -d 172.17.1.0/24 -o tun0 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 172.17.0.0/24 -d 172.17.2.0/24 -o tun0 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -d 172.17.0.0/24 -o eth0 -j MASQUERADEVPN Client1:
iptables -t nat -A POSTROUTING -s 172.17.1.0/24 -d 172.17.0.0/24 -o tun0 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 172.17.1.0/24 -d 172.17.2.0/24 -o tun0 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -d 172.17.1.0/24 -o eth0 -j MASQUERADEVPN Client2:
iptables -t nat -A POSTROUTING -s 172.17.2.0/24 -d 172.17.0.0/24 -o tun0 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 172.17.2.0/24 -d 172.17.1.0/24 -o tun0 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -d 172.17.2.0/24 -o eth0 -j MASQUERADE别忘了要打开ip_forword,iptables配置要保存至配置文件。
启动VPN:
VPN Server:、VPN Client1:、VPN Client2:
service openvpn start